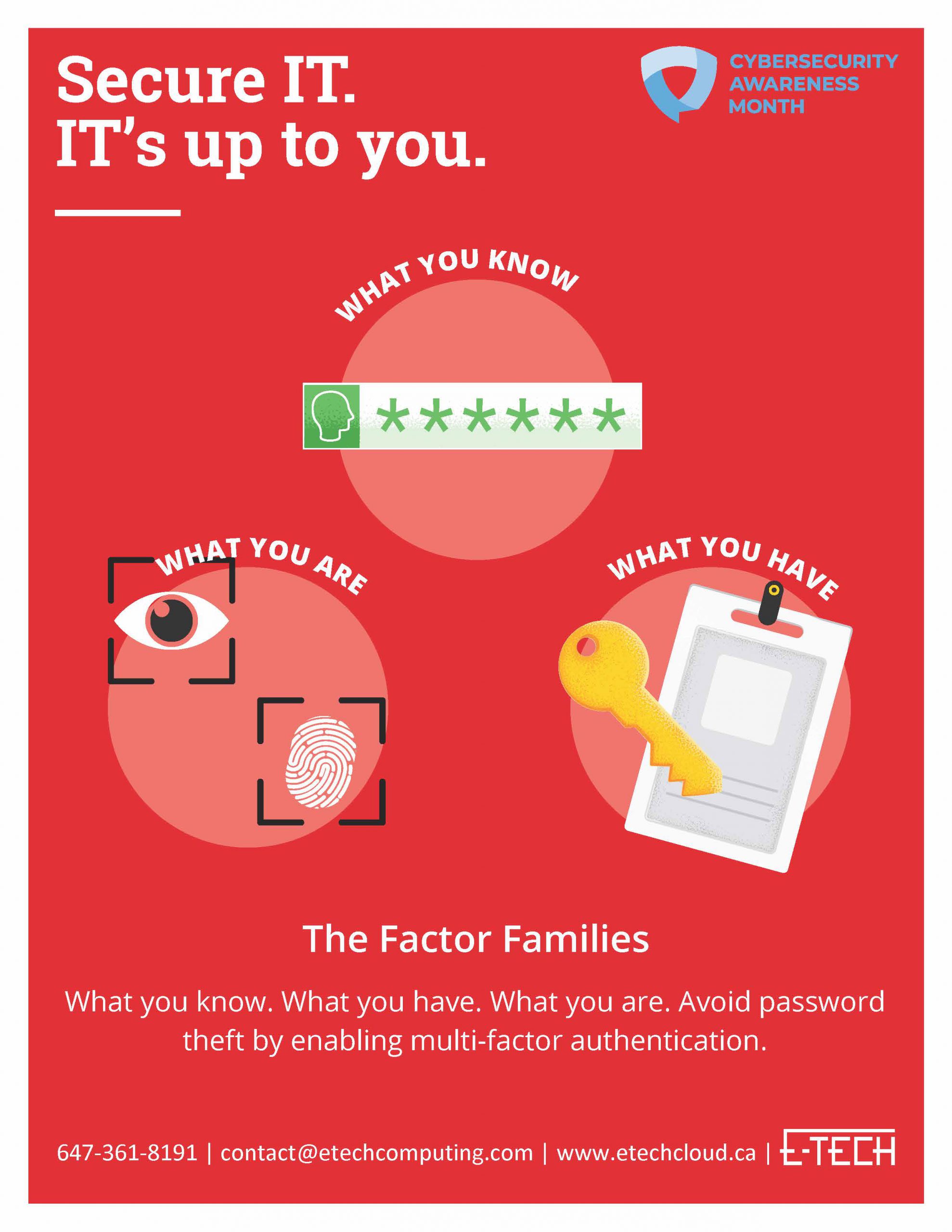
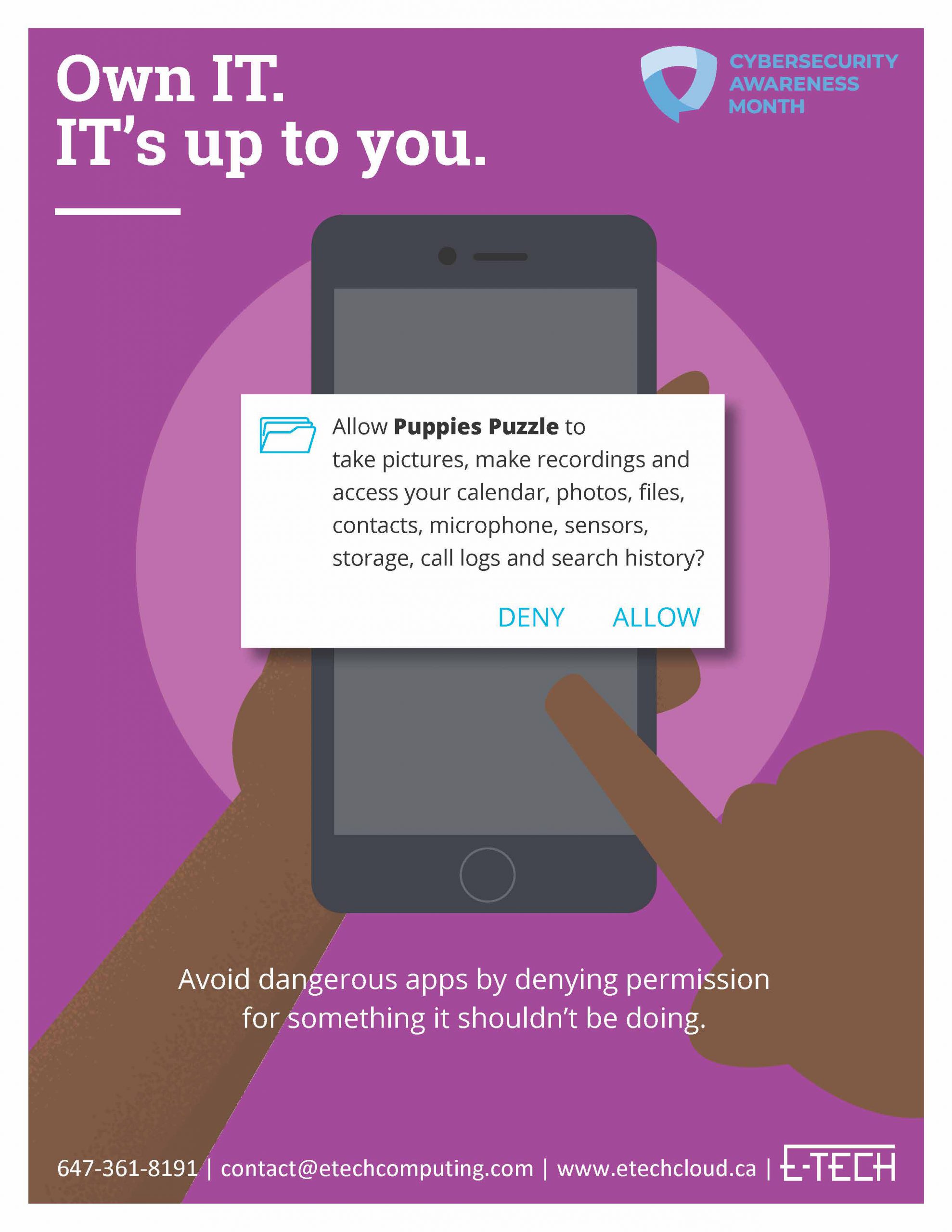
National Cybersecurity Awareness Month — a collaborative effort between government and organizations like ours to ensure everyone has the resources and knowledge they need to stay secure at work and at home.
When it comes to cybersecurity, knowledge is power. Here are 5 tips to help keep you secure:
1. Fishing and Phishing
Fishing is the art of dangling bait to catch a meal. Phishing is the art of dangling bait to catch a person. Phishers will impersonate friends, families, companies or authorities and dangle offers or threats to attract attention. Then, when someone takes that bait, the phisher harvests their information or money.
Thanks to the internet, phishing is very common today. Phishers send emails to engage you, asking you to click on a link or download an attached document. Bait includes financial incentives, offers of jobs or prizes, and warnings about needing to pay a bill. The goal is to harvest money and data — or get you to download malware which will infect your system.
Plain old skepticism is your best defense against phishing. Phishers want you to act quickly without questioning what they’re telling you, because their stories usually can’t hold up to closer inspection. Never download unsolicited documents or click on links in emails.
2. The Many Forms of Malware
Malware comes in many forms … and many disguises. Variants include computer viruses, worms, Trojan horses, rootkits and ransomware, but it all comes down to the same thing: malicious software invading your machine.
The main purpose of malware is to steal money, data, access and other valuable things. It may be either self-propagating or controlled by a remote attacker, but any form of malware attack on your system will be dangerous for you.
To protect yourself from malware, always use an updated antivirus and firewall. Enable automatic updates so that your system doesn’t miss crucial patches. But you have an important role in protecting your system, too: it’s important to never carelessly download files or permit random programs to run.
3. Social Engineering — And All Its Moving Parts
Sometimes, the most powerful tool is a word. Social engineers know that, and they use that tool to bypass all of the automatic protections and preplanned procedures you have in place. A persuasive lie can get an attacker further than a dozen hacking tricks.
Fighting social engineering is all about being skeptical and thinking clearly. Social engineers want you to act quickly and not question what they tell you. They use tactics like sympathy, intimidation, authority and urgency, pressuring their targets to make careless decisions — such as letting them into a restricted area or turning over valuable information.
When you ask questions and treat every request with healthy skepticism, you stop social engineers in their tracks. Ask them: “Can I see some ID?” Or say “I need to verify this with my supervisor.” Refuse to be taken in by a sob story or threats and insist on checking with your boss or the appropriate authorities.
4. Your Data is Valuable — Protect It
Thieves coming after your money is easy to understand. But why would someone target your data?
Many people don’t think of protecting data such as their email address, phone number or personal ID number. But these simple pieces of information are often valuable targets for attackers. All forms of data are valuable in one way or another: a phone number, for example, can help an attacker impersonate someone and search for more connected identity information.
Protect your data and the data of others that you may handle. You can do this by never giving out information to anyone without explicit permission. Knowledge is your best defense: be aware of the different ways attackers can target your data and the various tricks that they use to convince you to hand it over.
When in doubt, always double-check with your manager!
5. The Smart Way to Handle Smart Devices
Smartphones, smart appliances, smart homes … Is there anything that isn’t smart? Well, it turns out that relying on smart devices isn’t always that smart.
The Internet of Things, or IoT, is the new frontier in networking. Smart devices have internet capability, enabling them to network with computers, phones and each other. The purpose is to share data, making your life easier. Unfortunately, that data is not always secure.
The joker in the deck is the newness of the tech. Smart devices contain computing technology, but they aren’t always created and issued by companies that specialize in computers. Many smart devices ship with little or no security protocols.
IoT devices have already been implicated in several high-profile data breaches. Attackers can exploit weak cybersecurity and default passwords to break into the device. Then, once they have that access, they can leapfrog to the wider network and the other devices there.
When it comes to smart devices, the smartest thing to do is keep them safe and separate. Research the device’s security settings and credentials, and make sure that you’re using new, unique, strong passwords on each device.
Feel free to Contact Us for more information on Cyber Security Awareness Training.>