Facebook Gets Hacked – The 10 Best Ways To Stay Safe on Social Media
Social media needs no introduction – if you don’t have some sort of social media account by now, you might be living under a rock. Social media covers everything from casual sites (Facebook, Twitter), artistic sites (Instagram, Spotify), and even instructional sites (Waze, Reddit). What fails to be thought of by everyday consumers is how safe is it really?
It seems like every week, another big corporation announces a huge data breach, the most recent and most troubling being Facebook. On September 28th, initial reports by Facebook itself suggested that 50 million users were affected, and most recently (as of Oct. 12th) that number stands at a smaller but still unimaginable 30 million users [1] [2].
How did 30 million people get attacked?
As Facebook explained, hackers were able to exploit a vulnerability in Facebook’s code for the “View As” feature. The “View As” feature allows account owners to see how they’re profile would look like to other people. The hacker exploited this system by making it so if they were logged in as User A and did “View As” User Y, they became User Y. If User Y was logged in, the hackers now had stolen your Access Token, the generated cookie/tool that keeps your account logged in and from having to log in every time you load up Facebook [3].
Who was affected?
Facebook did a scan of all its users who used the “View As” feature in the past year, and deleted their access tokens. That resulted in 90 million users, whether they were hacked or not, experiencing a forced log out. Facebook recently reported that it estimates 30 000 000 affected by this breach.
[2]Out of the 30 million that were affected:
- 1 million had no Facebook data accessed at all.
- 15 million had at most their name, phone number and email addresses accessed.
- 14 million had contact details and other profile data accessed, including “username, gender, locale/language, relationship status, religion, hometown, self-reported current city, birth date, device types used to access Facebook, education, work, the last 10 places they checked into or were tagged in, [their] website, people or Pages they follow, and [their] 15 most recent searches.”
Just another of a long list of corporations, social media giants and e-commerce sites to be compromised, it leads us to question if we could ever be safe.
What does it take to have true cyber protection?
With social media, you almost have little control when the biggest of corporations are still vulnerable. With the skill, technology and organization of today’s cyber criminals, it’s not a matter of IF you can get hacked, it’s a matter of being better prepared than someone else. A hacker will not waste its time on a strong defense, especially when there are millions of weak ones.
Here’s the 10 Best Ways to Stay Protected on Social Media:
1. Use a strong password.
- This is the standard – cyber security 101, but it’s still overlooked by nearly all users. A hacker’s best tool is a brute force attack – an attack designed to discover a password through trying every single combination of letters/numbers/symbols. These attacks 8 BILLION combinations per second. A password should NOT consist of words or phrases. A great way to choose a password and remember it is to pick your favourite line from a movie/book, take the first letter of each word, capitalize every 3rd letter, and then repeat. For example; “O Romeo, Romeo! Wherefore art thou Romeo?” = orRwaTroRrwAtr.

2. Use a different password for each of your social media accounts.
- Nearly 80 percent of users use the same, or a variation of one password across several accounts. If a hacker can steal one password, how hard would it be for them to get the 10 other similar ones? You might as well hand it over to them.
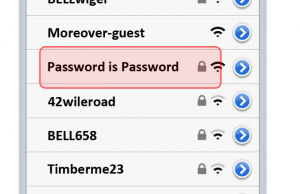
3. Never log in from wifi networks you don’t know and be wary of free networks.
- Anyone can purchase a portable wi-fi adapter from their service provider. There is nothing stopping a criminal from going to your local Starbucks and naming their portable network “Starbucks Free Hi-Speed Wifi.” Next thing is, you logged in to that network – of course you did because it was Hi-Speed – and you’ve now given access to your phone to hackers.
4. Be wary of third-party add-ons and apps.
- That follower tracker you downloaded to track your twitter followers could be developed and designed to trick you into giving up your account information. In fact, in 2017 alone, Google took down 700 000 malicious apps on it’s Play Store that were used for criminal activity.
5. Check your privacy settings.
- Often overlooked are the privacy settings on your social media accounts. The more private you are, the less likely some can steal your information, it’s as simple as that.
6. Don’t click that suspicious link!
- I admit that I also want to read “10 Reasons Why Star Wars is the Best Series Ever,” but it could mean clicking a link that’s going to download viruses, malicious software, encrypt your files or even destroy everything all together.
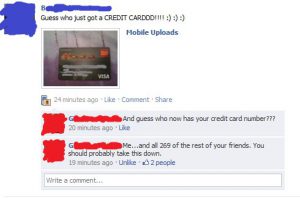
7. Be careful about what you share.
- Don’t reveal sensitive personal information ie: home address, financial information, phone number. The more you post the easier it is to have your identity stolen. Believe it or not, posts like this exists:
8. If you have social media apps on your phone, be sure to password protect your device.
- To have a cellphone constantly unlocked is asking someone to steal it. The best protection are the alphanumerical passwords that are available on most smartphones.
9. Remember to log off when you’re done.
The 30 million who got compromised through Facebook could have been safe if they did this simple thing. If it’s an important account, always log out when you’re finished. You can be the most secure, but all a hacker needs is your Access Token, and then they have your account.
10. Keep your firewall security and anti-virus software up-to-date.
When all is said and done, you must have proper anti-virus/anti-malware protection. Watch out for fake software being sold online – those are run by hackers as well. Always buy from a trusted source.
Contact Us to find out if YOUR corporate email address is being sold on the DARK WEB for hackers!