What is the Dark Web? – Screenshots from the Dark Web
With all of our seemingly trustworthy big businesses constantly getting attacked by cyber criminals, you may have wished upon a star for a place on the internet where you are untraceable – a place you can explore with complete anonymity. That virtual haven is known to its users as the Dark Web.
Although complete anonymity is nearly impossible, surfing the Dark Web is the closest you can get to it. But what is it? To understand the Dark Web, you must have a good understanding of how the internet works.
When we’re looking at the internet, a great analogy to use is the famous iceberg:

Looking at this iceberg – what the common user thinks the whole internet consists of is actually only the Surface Web. This is the portion of the World Wide Web that is readily available to the general public.
What it consists of is anything you can access for free, which is also why its called the Open Web. Most of the websites you can access on search engines like Google and Bing, these are all considered to be part of the Surface Web.
We are all familiar with this part of the internet since we use it to run businesses and connect with family, friends, and customers, and much more. But what’s crazy is that The Surface Web only consists of about 4% of the information that is on the internet.
Now as we start to move below the surface on our iceberg, an estimated 96 percent of the internet lives here in what is called the Deep Web. No one really knows how big the Deep Web really is, but it’s hundreds (or perhaps even thousands) of times bigger than the Surface Web.
What this part of the internet consists of is data that you won’t be able locate with a simple Google search and is not open to anyone to access. Most sites that require credentials to get into can be categorized as the Deep Web.
In reality, most of us use the Deep Web everyday without even realizing it with things like email, online banking, and pretty much everything that requires a username and password to access.
There’s a flip side of the Deep Web that’s a lot murkier, and sometimes darker. This is why it’s known as the Dark Web. That is represented by the bottom portion of the iceberg.
In the Dark Web, the users really do intentionally bury data. Often, these parts of the Web are accessible only if you use special browser software. You won’t be able to get the dark web websites with Google Chrome, Mozilla Firefox or Internet Explorer. The most common dark web browser is called the Tor Browser, and what the Tor browser does is it makes the user anonymous, so it becomes extremely safe for criminals.

However, the dark web isn’t all bad; it’s used for an array of purposes of everyday people. For example, journalists use the dark web to help protect their sources, there are social media websites, and the government may also use it in whistle blower situations.
But unfortunately, the dark web carries a notorious reputation as the haven of criminals, terrorists, nefarious sites, and everything in-between. It is a huge marketplace for stolen data and personal information. After a data breach or hacking incident, personal information is often bought and sold on the dark web by identity thieves looking to make money off your good name.
The Dark Web attracts all types of crime, simply because of the anonymity of it. In fact, it’s estimated that 50% of all Dark Web sites are used for criminal activity. This criminal activity can include the selling of narcotics, illegal weapons and firearms, hired assassins, child pornography, malware, and anything else cyber criminals can do over a wired connection.
How does this cyber criminal underworld affect you?
When data breaches occur to big corporations, the credentials, SIN, banking info, etc. – it all starts to get sold all over the Dark Web. That stolen data is then used to steal your identity, your money, and further spread the computer diseases to your friends and colleagues.
Just to show you how legitimate the sites are on the dark web, we’ve taken some screenshots to share with you!

This dark web website is called the Clone Card Crew, and it’s a criminal website where you can buy and sell real credit cards. The selling of Credit or Debit card information is very popular on the dark web, with this site selling information from $5-$110.
What they’re selling is a “full” package purchase for the fraudsters: including the stolen name, SIN, birth date, account numbers… really anything you need to use the card effectively. Sites like this will even discreetly mail you the card, so your neighbors have no idea what you are up too! And to ensure the validity and trustworthiness in the purchase, buyers can even leave reviews for sites like these, similarly to how someone would leave your company a google review!
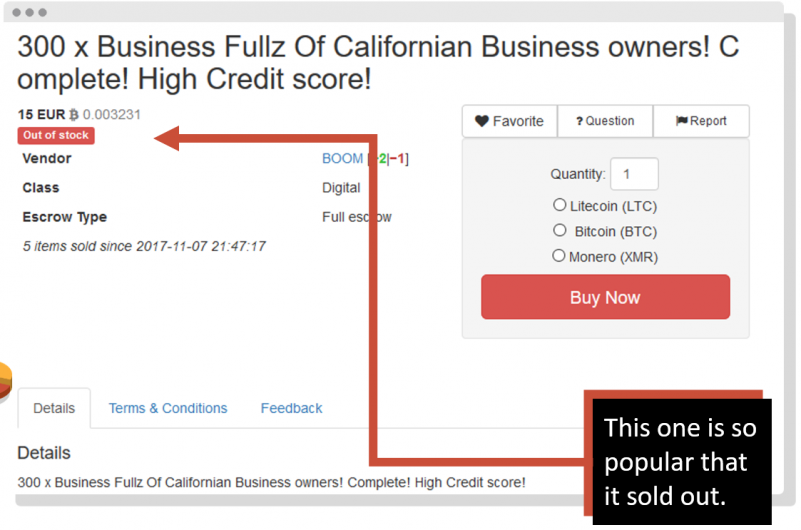
This is an example of a post on the dark web were a cyber criminal is selling 300 “Fullz” of Californian business owners. The word fullz is a slang term used by credit card hackers and data resellers meaning full packages of individuals’ identifying information. Fullz usually contain an individual’s name, SSN or SIN, birth date, account numbers and most other data. With this post in particular, the price was extremely low; for only 15 euros, you can steal the identity of 300 people and possibly ruin their lives. As we can see, it was so popular that it sold out.
How can you stay protected from the Dark Web?
Here’s a step by step process to ensure greater security:
1 – Knowledge is Power:
With our Dark Web Monitoring, you can receive up to the minute alerts as to when your business credentials are being sold on the dark web. This is one of the best ways to stop cyber attacks towards your business before they happen.
Register for a free domain check to see if you or your organizations credentials are being sold over the Dark Web.
2 – Password Protection is key:
About 80% of people will use the same password or a derivation of the same password for multiple different services [2]. This makes it extremely easy for hackers to gain access to multiple services if they buy only one on the Dark Web. “P@ssw0rd1!” is not hard to crack – check out our password tips to become more secure.
3 – Use multi-layered security solutions for your services:
This is great protection in the event that a cyber criminal gets access to your credentials and is actively trying to log into your accounts. Wherever possible, enable 2-Factor Authentication or Multi-Factor Authentication.
For example; you can set most of the popular social media websites to send you a verification text message every time your account is signed into, to ensure that it’s actually you signing in. This extra layer could be the difference between safety and a huge cyber attack.
4 – Keep your software up to date: In 2017, the infamous Wannacry ransomware ran rampant throughout the world whereas over 150 countries and over 200,000 organizations were impacted. This was simply because the hackers found an exploit in older Windows operating systems. Security updates can seem mundane, but they’re there for an ever-important reason.
Antivirus services are constantly finding new threats and updating their procedures. Make sure to update your software so you are protected from the newest and more sophisticated threats.
5 – If you’re breached, call in the experts:
When you deal with cyber crime, it’s especially hard to fight back without the help of an expert. Not everyone or every organization can spend all day thinking about security, but there are experts like E-Tech who do.
Feel free to Contact Us for more information.








