A Criminal’s Weapon – The Biggest Cyber Security Threats
How unsafe is the internet really? How much damage can be done online?
The internet is much more unsafe than it was 20 years ago. Cyber crime has risen year after year and has evolved every step of the way. Cyber criminals are so smart, and modern-day technology introduces so many new innovative threats to be wary of. Cyber War is real, and we are engaged in battle. It’s important to know who you’re fighting against, what weapons they are using, and what you are fighting for.
 Who Are Cyber Criminals?
Who Are Cyber Criminals?
Who am I protecting myself from? How much power do they have?
The picture to the left depicts the stereotypical image visualized when someone says “hacker”. Like all crime, there are many individually driven criminals. But also like all crime, it has evolved to become more organized. For example, some of the most recognizable organized hacker groups are Anonymous (although they commit crimes that are more activist in nature), and Morpho (known for hacking Microsoft, Apple, Facebook and Twitter) [1]. These organizations are extremely powerful, enough to successfully attack governments and major corporations.
 What Are Cyber Criminal’s Motives?
What Are Cyber Criminal’s Motives?
How much is my data worth?
There are many theories as to why people become criminals, but what is undeniable is the volume of opportunity cyber crime can generate for a common lawbreaker. A huge motivation is potential financial gain. Cyber crime has become so big and powerful that it is estimated that global cyber crime alone generates 1.5 TRILLION dollars annually[2]. It’s also undeniable that it’s harder to physically steal someone’s wallet and get away with it than it is to steal their credit card information online and get away with it. Criminals are much braver behind a screen, and there are many ways that they can keep anonymous and commit crimes.
What Are The Biggest Cyber Security Threats Against Me?
What are the ways I can be attacked? How can I be protected?
1. Phishing emails and social engineering attacks
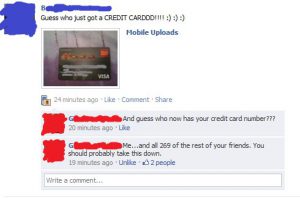
Almost everyone has received one of these spam emails: an email requesting either information, login credentials, banking information, etc. You can see from the red texts that this is clearly a scam. Phishing emails often have spelling mistakes, incorrect email domains and suspicious links. Here, we tell you how to identify phishing emails. These attacks have become more sophisticated. Cyber criminals will impersonate someone close to you, a mother, a boss, etc., and email you from an impersonating account.
2. Distributed Denial of Service Attacks (DDoS)
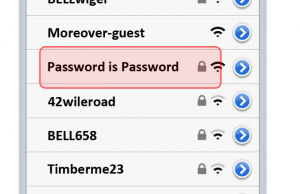
This is the technical term to overload an online service by overwhelming it with traffic from multiple sources. In physical terms, it’s like closing a highway because there’s too much traffic on the road. Cyber criminals will do this to shut down your network, and it’s even something that can be bought over the Dark Web to commit to someone else’s servers if you had the mind to.
 3. Ransomware
3. Ransomware
Like a simple, physical ransom, criminals will take something of importance to you and demand you to pay them back. In cyber crime, what’s important is your data. Cyber criminals will encrypt your files on your computer making them accessible only to them, and demand you pay them to get your files back. This can be extremely costly for business, and in fact most 75% of small to medium businesses report a ransomware attack has led to business-threatening downtime. Discover how to protect your business from ransomware.
4. Cryptojacking
With the emergence of cryptocurrencies like Bitcoin, Ethereum and Ripple, etc., has created another way that cyber criminals can remain anonymous online. Cryptojacking is the unauthorized use of another’s computer to mine cryptocurrencies, or cryptomine. Cryptomining, in the simplest terms, is the process of creating new cryptocurrencies – and once completed, you are awarded with currency. This requires a large amount of computer processing power, so cyber criminals will trick you into downloading scripts onto your computer to use your power.
5. Data breaches
Large corporations fall at the hands of hackers seemingly every week. One of the biggest data breaches to date was Facebook, where 30 million users were compromised. You can find out here the 10 best ways to stay safe on Social Media.
 6. Viruses & Malware
6. Viruses & Malware
There are so much computer viruses and malware nowadays that modern computers are bought with a trail run of an antivirus software, like Webroot. Viruses and malware can attack in many ways, from deleting files, to shutting down your whole device. Ensure your antivirus programs are always up to date and do routine scans of your devices.
Feel free to Contact Us for more information.



 6. Viruses & Malware
6. Viruses & Malware