Website Security
7 Types of Cyber Security Attacks with Real-Life Examples
With every passing day, cyber crime is a continuingly increasing methodology in the criminal industry with no signs of slowing. Every day, there are new tools and strategies that allow cyber criminals to target you and your company’s data with increasing success rates. You may be asking yourself, Why do criminals want my data? As society continues to progress with technology, the data produced also increases in value drastically; which directly correlates to how much you integrate your daily life and/or corporate life with online tools and apps. With the above mentioned, sometimes it gets to a point where separation from their data, people and businesses cannot function; thus putting themselves at a severe disadvantage against their competitors. With the high and rising value of data, the risk of losing it increases as well. How? Cyber crime! Having no cyber security plan for you or your business is like a bank with an open vault. Knowing what kind of attack criminals can use is key to keeping you and/or your business from falling victim to these crimes.

Malware
Malware can be described as any malicious software that is installed on your device after a user may click on a dangerous link inadvertently or open an attachment. There are many forms that malware can take, with some of the most common being Viruses and Trojans. Viruses are coined after biological viruses, in that they replicate themselves, and can infect applications in the user’s device. Trojans, or Trojan horse malware term came from the ancient Greek story of the fall of the city of Troy due to the deceptive trojan horse. This malware spreads by pretending to be a useful software while secretly containing malicious instructions. In July 2016, a Japanese travel agency, JTB Corp, suffered a data breach compromising almost 93 million user records. The data breach was a result of an employee opening a malicious document which he received via a phishing email. The malicious document included a trojan horse, that is designed to steal user information. It was reported that 7.93 million user records from Japanese Travel Agency were compromised. 1
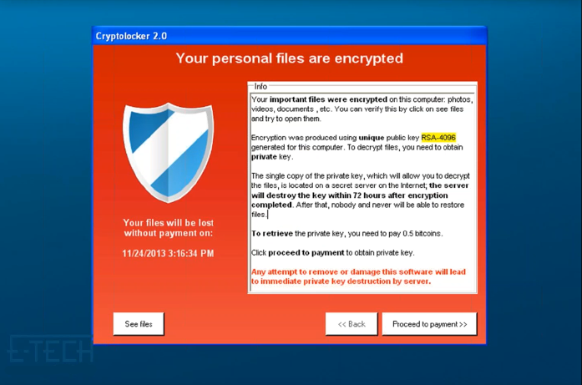
Ransomware Attacks
Ransomware specific type of malware that gains control of your system and blocks access to your files. It can infect your computer from an email attachment or through a bad website. Upon infection, a ‘ransom note’ pops up, offering to restore your system back to normal in exchange for compensation. With ransomware, we always recommend to never pay the ransom! Why? There is absolutely no guarantee that you’ll get your files back. You simply cannot trust a criminal to adhere to their promises. Secondly, you’ll be putting a target on your back. If you pay the ransom once, you’ll be flagged as a user who pays the ransom, and the criminals will be back to take advantage of you again.

This is an example of Ransomware and this was called the WannaCry attack, and at the time it was the biggest ransomware attack ever. It hit earlier in 2017 in over 150 countries and over 200,000 organizations. How did this even happen? Well, the hackers found an exploit in older Windows operating systems that had already reached its end of life. When an operating system reaches its end of life, it means the company is no longer making security updates. Why is this important? A lot of people and companies continue to not update their systems. Its so important to update all your operating systems from your Samsung Galaxy, Windows desktop, iPad or iPhone and everything you use on a daily basis with critical updates to keep your systems protected.
Man in the Middle Attacks
The man in the middle attack is where a cyber criminal is intercepting your data or information while it is being sent from one location to another (ie. communications system to a server). This type of attack is very common with vulnerable Wi-Fi connections like at coffee shops, hotels, and restaurants. While your out in public, always be wary of open Wi-Fi networks. These can be set up as traps by cybercriminals to lure people into accessing websites with sensitive information, all the while they are snooping on your activity. In 2017, credit score company Equifax removed its apps from Google and Apple after a breach resulted in the leak of personal data. It was found that the attackers were intercepting data, in the form of a man in the middle attack, as users accessed their accounts. 2

Distributed Denial of Service (DDoS)
In this cyber attack, the criminals are basically trying to overload the system you would have in place, either it be a website, server, etc., with traffic. This will typically cause the system to crash or shutdown, resulting in downtime. These types of attacks typically do not result in stolen information. Most of the time, these attacks are a form of bombardment from the cyber criminal meant to shut your system down, resulting in lost revenue from downtime and recovering your files. On Sept. 9, 2021, there was a huge cyber attack on the Russian Tech powerhouse, Yandex, and is believed to be the biggest DDoS attack ever seen. Yandex reported that their “experts did manage to repel a record attack of nearly 22 million requests per second (RPS). This is the biggest known attack in the history of the internet.” 3
Password Attacks
This can be described as any attack designed to steal a user’s passwords or credentials. There are basic techniques that even non-hackers can use like manual guessing. This is where a bad actor can guess your password based on the information they learn from your social media. Or even basic shoulder surfing, where someone literally watches you as you type in your password, or even if you have a sticky note of your password on your desk. And there are more advanced techniques like a brute force attack. This is where a hacker has a program that can guess literally millions of passwords at a time. That’s why we say that having a weak password is like not having a password at all. They can even use programs that have key logging. This is when you’re on a malicious website or even if you’ve accidentally installed a key logging program, and now the hacker can see anything you type. They’re basically waiting till you go to your banking website or social media and type in your credentials.
Back in August of 2021, the Canada Revenue Agency was a victim of a password cyber attack, whereas their online systems were shut down for several days, and over 5000 accounts were compromised! This was due to the technique called credential stuffing. This is where the hackers buy or steal users’ passwords from other sources and data breaches, and they use those passwords to try to log into the CRA accounts. This can be a huge problem, especially if users use the same password across multiple platforms.

Drive-By Download Attacks
Drive-by attacks happen when you’re surfing the internet and enter a website that has malware code on the page, and you inadvertently download the code. It is also one of the most common ways of spreading malware. All the hacker has to do is to plant code on the page. A common example of this is when you’re on a website and an ad pops up that has nothing to do with the site’s information. Most times, clicking the ad will result in malware being downloaded onto your computer. Unlike other cyber-attacks, a drive-by attack does not need you to do anything to enable the attack on your computing device.
A popular form of drive-by attack is cryptojacking. This is where there is code on a website that is stealing your device’s processing power to mine cryptocurrency. Mining cryptocurrency requires a lot of processing power, so this attack is not designed to steal any information from you, but rather steal your computer’s power. If you’ve read this post and you’re thinking you need help with keeping your network secure, contact us to get professional help!