Last week one of our client’s LinkedIn account and Office 365 email account was compromised by a phishing scam. An email was then sent from this user’s compromised Office 365 email account with the subject ‘John Smith has shared “CEO Emails” with you’ with a PDF attached containing a link to log into a Dropbox account to view this document. This email went out to all contacts this compromised user has ever emailed from their Office 365 email account.
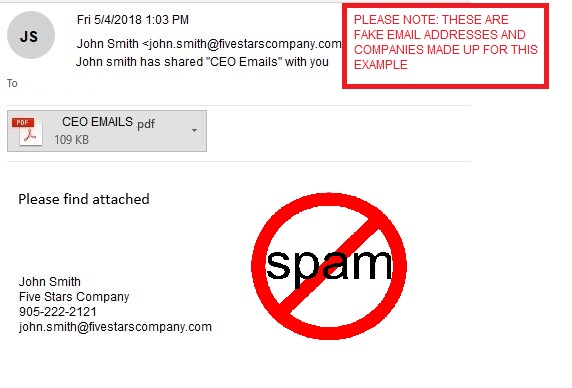
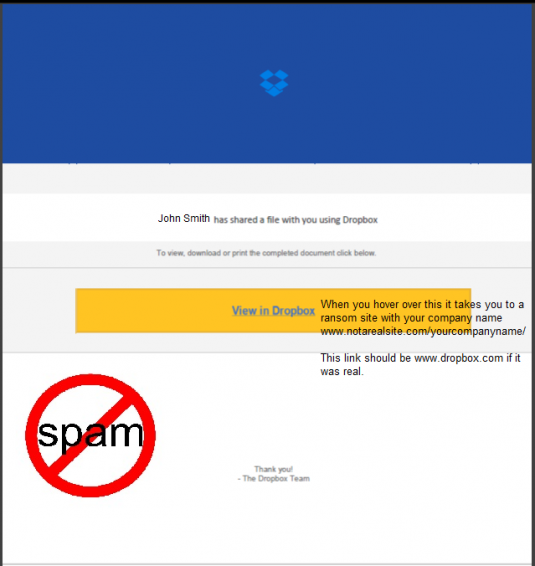
Some recipients who received the email and felt it was suspicious replied to the user’s email address, and the recipients received one more email confirming that in fact ‘It is legit. Please proceed to view in Dropbox’ from the user’s compromised mailbox. The hacker gained access to the user’s email and sent out reply emails confirming the Dropbox email to try and trick people to get more credentials. The hacker also added a rule to move all incoming emails to the delete folder. If you entered your information into the Dropbox screen it would tell you ‘please try again later, the services are down’.
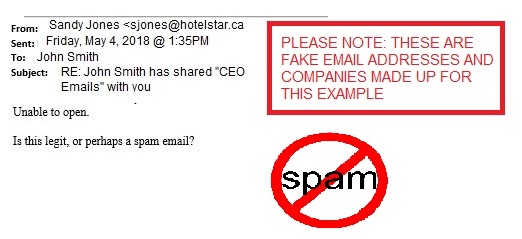
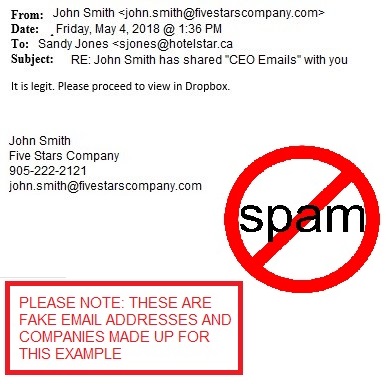
One of these phishing emails were also sent to our E-Tech Helpdesk Ticketing System and we were in contact with the client right away. We reset the user’s compromised mailbox password and the user changed their LinkedIn Password. We increased the security and compliance to the next level, by enforcing two-factor authentication and enforcing password policy. We scanned this user’s computer for malware and viruses, but nothing was found. We confirmed that the malware/virus is quarantined at Office 365 cloud by generating anti-malware, anti-virus, and spam reports from Office 365 and confirmed no other mailboxes were compromised.
The best tips to avoid this type of Phishing scam are to:
- Enforce password policy every 42 days
- Enforce Password complexity (using symbols, capitals, numbers etc.)
- Enforce Two-step Factor Authentication on both your personal and work emails
- Open only Microsoft documents (Word, Excel, PowerPoint), and Adobe (PDF)
- If you receive PDF or word document attachment, make sure it’s making sense to you and relates to your work (hover over the link first to see where it will take you, example: if its Dropbox it should say https://www.dropbox.com LinkedIn should be https://www.linkedin.com)
- Avoid opening social media links attached in the email or inside PDF, or word document files
- Pay attention to the sender email address that is in the ‘From:’ address box, and the domain that the email was sent from (hover over the email address, see if its legit, example: if its Dropbox it would say someone@dropbox.com if its LinkedIn it would say someone@linkedin.com)
- Pay attention to the content of the email. If you see grammar mistakes, please confirm with the sender and mark this email as spam (instead of replying to the email you’re not sure about, call the user or email them in a new email thread)
Here are some links for more information on Phishing Hacks:
https://www.microsoft.com/en-us/wdsi/threats/support-scams
https://blogs.technet.microsoft.com/office365security/how-to-deal-with-ransomware/
https://dev.etechcomputing.com/how-to-identify-phishing-emails/
https://dev.etechcomputing.com/beware-phishing-scam-for-office-365-users/
Feel free to Contact Us for more information.












